Member-only story
PenTestMonkey & Ivan Sincek Shells Failing? Use This PHP Reverse Shell
You managed to find a LFI or a way to upload a php malicious file via ftp. You are very excited because you are about to get a foothold. You tried our “old friend” PHP PentestMonkey (it never fails). Until now, lol. No problem. We have the ace under the sleeve: Ivan’s multi Os PHP reverse shell. You tried, no luck. I’ve been there. Maybe the outgoing ports are not open. Maybe the PHP engine does not interpret those reverse shells properly. Not all is lost. Keep reading. Try this one instead.
The Problem
I try to stay away from web shells — for obvious reasons. I prefer a fully interactive session; you get more bangs for your bucks. But sometimes, that’s just not possible. Outgoing ports are blocked. Or the box simply doesn’t “like” the PHP reverse shell I’m using. I recently ran into this issue:
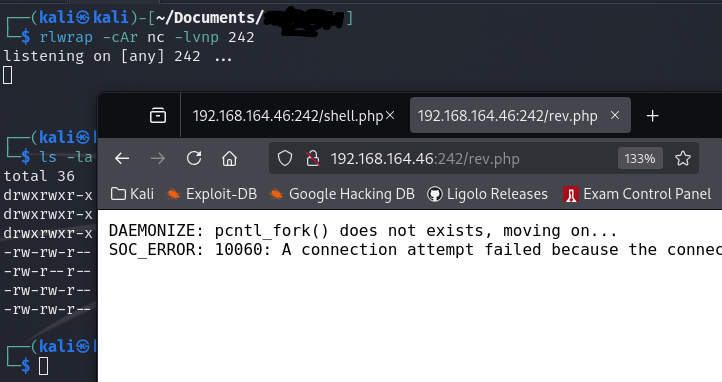
There’s still hope. We can upload and use a non interactive shell instead. It may not be as functional as a full reverse shell, but it’s better than nothing. We can still do some enumeration. And if we’re lucky, we might find hidden credentials or escalate privileges due to a misconfiguration or vulnerability.



![OSCP vs HTB CAPE’s [Certified Active Directory Pentesting Expert]](https://miro.medium.com/v2/resize:fit:679/1*NKzJkpq85g6kbm0t3sjrqQ.png)



